1. In-house or remote security operation center for monitoring their activity like transactions, attacks/threat to the bank:













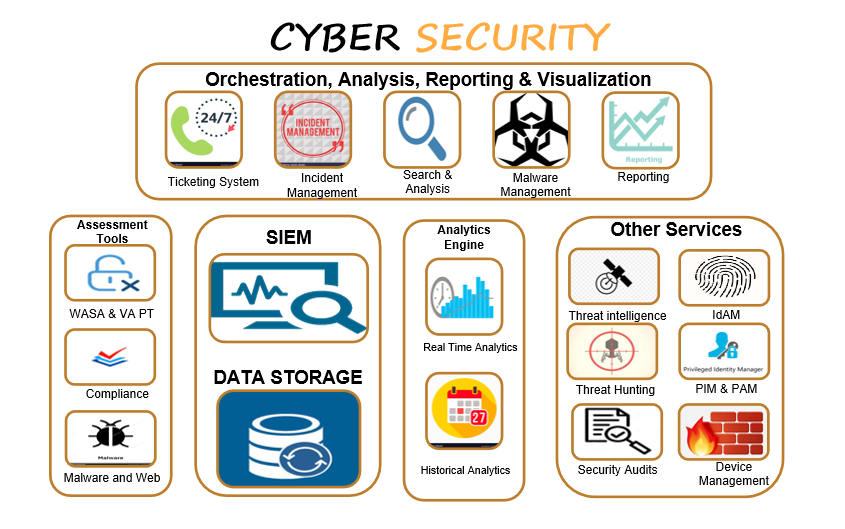
5. PIM and PAM solutions
a. PIM- Privileged identity management (PIM) is the monitoring and protection of superuser accounts in an organization's IT environments. Oversight is necessary so that the greater access abilities of super control accounts are not misused or abused
b. PAM: Privileged Access Management (PAM) is a solution that helps organizations restrict privileged access within an existing Active Directory environment.
c. Managing and deploying the tools for pim and pam
9. Device management
a. Management of network devices and configuring network devices for the client.
b. Network devices like firewall router switch etc
10. ISO 27001 :
a. Audit for 27001 information security can be carried out as internal audit or a second party audit for the bank